AmateursCTF

Table of Contents
Web
Denied
Challenge Description
what options do i have? http://denied.amt.rs
Solution
When looking at the source code, we see that the only way to get the flag, is to send a get request without req.method == "GET". A quick google search for all the HTTP methods reveals the HEAD method, that is essentially the same a GET request, but without a response body.
In Burp Suite, we can try to change GET to HEAD, and hope we get the flag.
Our initial request looks like this:
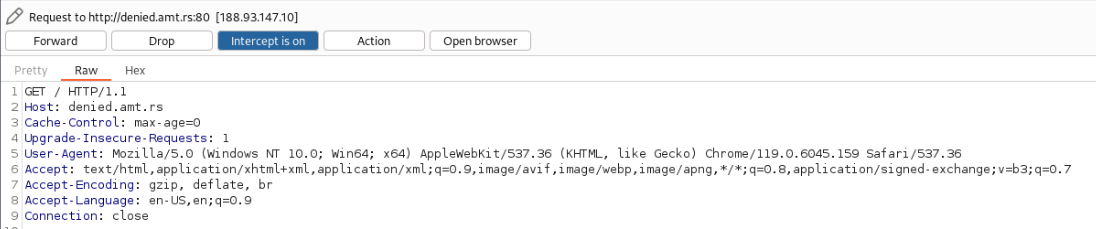
If we let this request through, we will just get the "Bad!" response.
But if we change the method to HEAD like here:
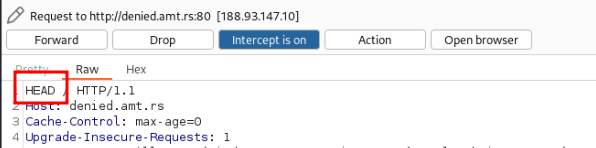
And forward the request, we get the flag in our response cookies.
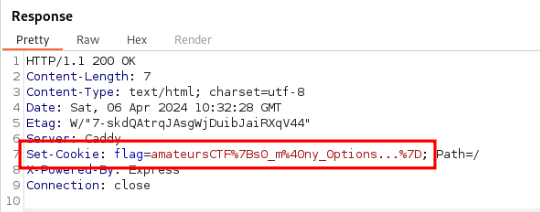
If you hover over the URL Encoded flag, you will get the decoded version: amateursCTF{s0_m@ny_0ptions...}
OSINT
Bathroom Break
Challenge Description
I was on an in-state skiing trip with my family when we decided to go out and see some sights. I remember needing to go to the bathroom near where these pictures were taken and then leaving a review. Can you find this review for me?
Solution
I started out by checking the exifdata for both images, just in case, but there wasn't anything useful.
Then i decided to use Bing Visual Search, which i have had some luck with in the past. When selecting the given images, a lot of results of "Hot Creek California" and "Hot Springs California" came up. I decided to search for the results on google maps, and found out that "Hot Creek California" revealed a nearby toilet, as described in the challenge description.
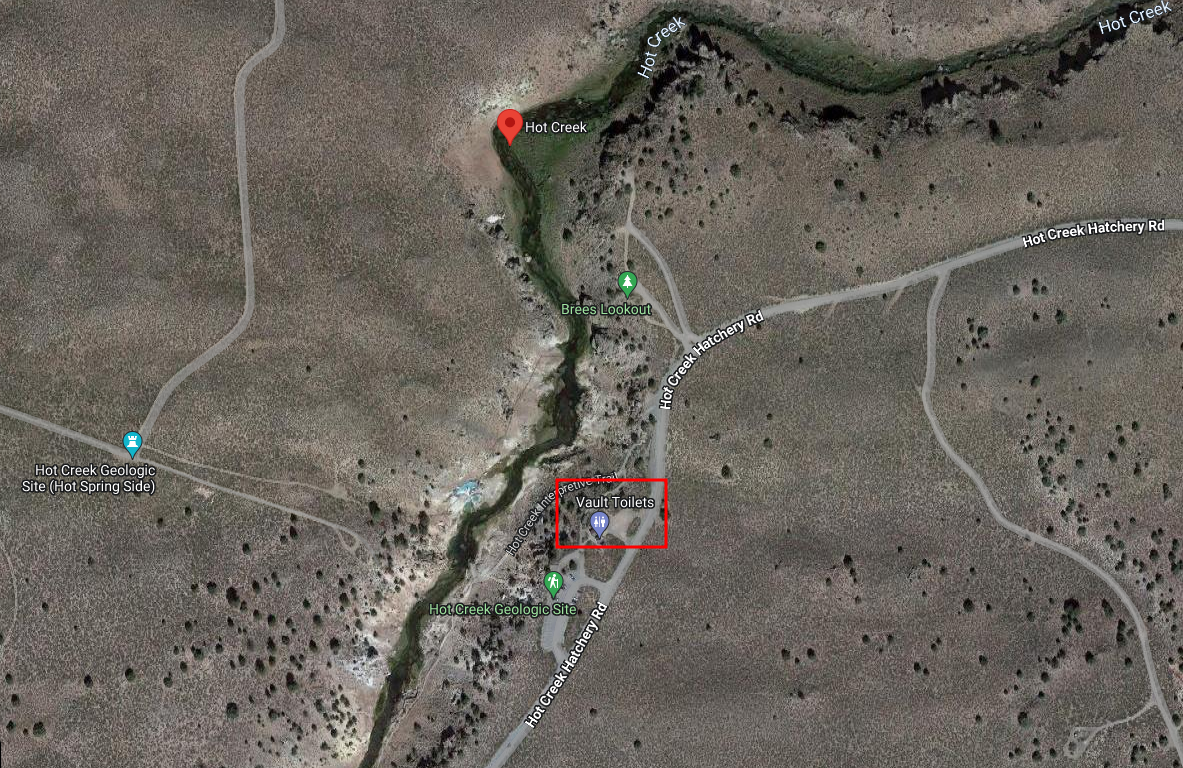
Clicking on the toilet, will reveal its reviews.
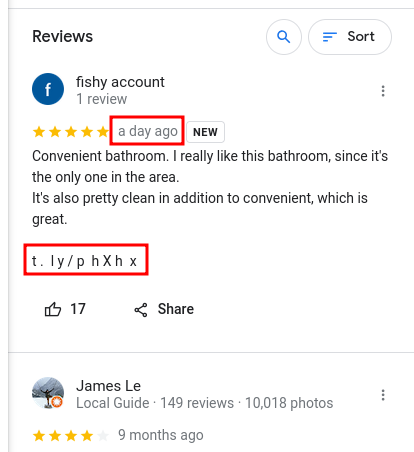
With the most recent being made a day ago. The account is called "Fishy account" and there is a link in the bottom of the review. It must be the review mentioned in the challenge description.
The link: t.ly/phXhx, reveals a pastebin with a lot of text, where the flag is located near the end.
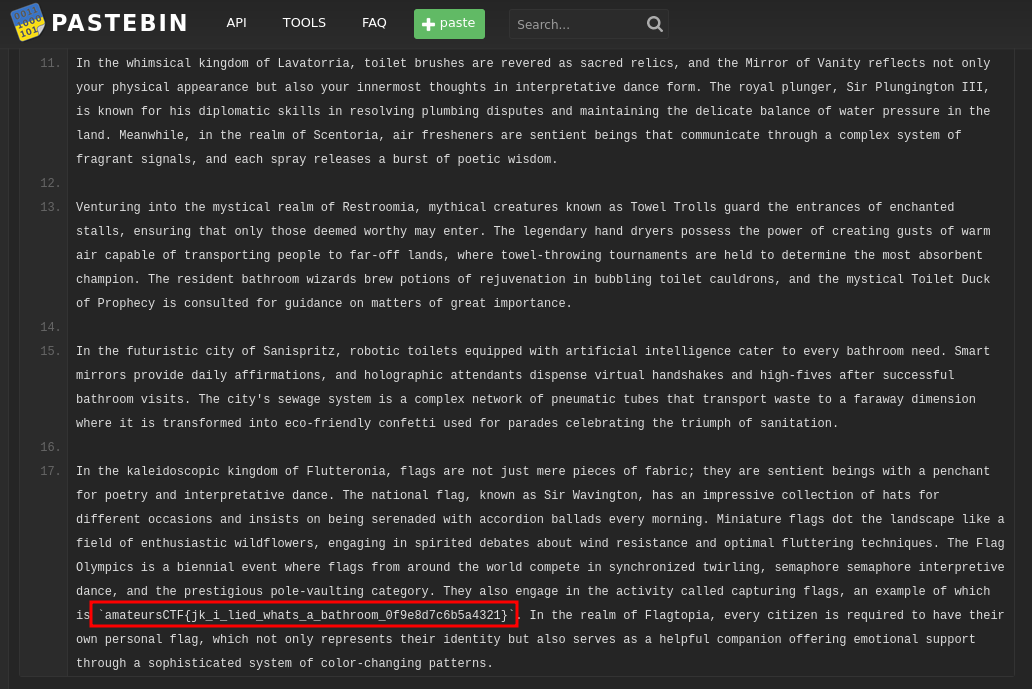
amateursCTF{jk_i_lied_whats_a_bathroom_0f9e8d7c6b5a4321}
Cherry Blossoms
Challenge Description
average southern californian reacts to DC weather. amazing scenery though at the time.
Find the coords of this image!
Grader Command: nc chal.amt.rs 1771
Solution
The image shows a cherry blossom tree near a circular formation of American flags, which is located at the Washington Monument.
After "walking around" using streetview. I found this location which seemed to be somewhat correct, the buildings in the background pretty much matched up with the given image, and to the right side, there is an area where people can stand, which also lines up with the given image.

When viewing the code, we see that we have a small fault tolerance. Just to try, i got the coordinates of the image: 38.889050, -77.033522, and pasted it into the server. The blurred part is just some useless Proof of Work stuff.
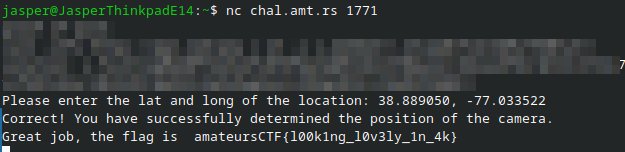
This answer is accepted, and we get the flag: amateursCTF{l00k1ng_l0v3ly_1n_4k}
Wumpus Leaks
Challenge Description
hopefully redacted enough, im kind of bad at this whole iphone photography thing so it took a few attempts to make this intentionally cringe msfrog in front of the flag, hopefully no one can guess the flag using this info
IMG_7276.jpg Clean your monitor bro
Solution
The given image was taken with an iPhone, according to the challenge description, which means that the flag should be stored in a iPhone image as well. I first looked up the iOS image naming convention, which is just IMG_XXXX.jpg where XXXX is the image number starting from 0.
My first thought was just to bruteforce the image name from IMG_0001.jpg to IMG_9999.jpg, but then i noticed the image name of the given image, which is IMG_7276.jpg. The description mentions, that it took "a few takes", which should mean that if we just count down, we should get the cached image.
Unfortunately i found out that discord has changed the way, that image urls work. It is now "signed", you can read more on their developer documentation.
This essentially means, that it's not possible to paste in the image name with a changed number and get the image. The image will only show, if you have the signed url. Since the signed url would be basically impossible to bruteforce, i found another method. Apparently when you send the unsigned attachment url on discord, it will show up like in the image below:
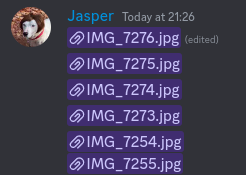
When you click the attachment thing now, you will get a signed attachment url. We should now just be able to cycle through some numbers and get the image.
I went from IMG_7276.jpg to IMG_7262.jpg which turned out to be the correct image with the flag. The full url for this image is: https://cdn.discordapp.com/attachments/1098086661847535719/1226012804150984754/IMG_7262.jpg?ex=66233866&is=6610c366&hm=6527d4ba198e337ce845ffe6962db629a1b9db5626e29bdb76cd2db67fbb92bd&

Flag: amateursCTF{s1gn1ng_a1nt_g0nna_st0p_0ur_brut3}
