Space Heroes CTF
Challenge files and containers can be found on FITSEC's Github: https://github.com/FITSEC/spaceheroes_ctf_23/

Table of Contents
Reverse Engineering
Acheron
Challenge Description
While researching a foreign planet, you and your team discover a cave with some strange eggs. Upon inspection, something attacked your team. You got separated from them and knocked unconscious. Once awake, you begin running to your ship to regroup with your team. The problem is, you don't remember the way. Find your way back to your ship.
from pwn import *
p = remote("spaceheroes-acheron.chals.io", 443, ssl=True, sni="spaceheroes-acheron.chals.io")
p.interactive()Solution
First thing to do is to create a python file with the content showed in the challenge description in order to get the flag from the server.
You can try to run the file and see that it needs navigation instructions in order to get the flag.
Since we have access to the executable running on the server, we can try to use a decompiler and see if there is anything interresting. I tend to use dogbolt.org, it tries to decompile the executable using different tools. When uploading the file, i look through the different decompiler content, and find Ghidras content interesting.
We can see excactly what the program want's as the input, just reading through the many if statements and writing down the different letters we get the following string: NENWSSEWSNENSSWEENWSNNESS now paste the string into the python script, and you will get the flag.
Crypto
Bynary Encoding
Challenge Description
Starfleet has received a transmission from Bynaus. However, the message apears to be blank. Is there some kind of hidden message here?
Challenge Solution
I first looked at the transmission.txt file, and noticed that is was filled randomly with whitespace. I also noticed that there was 2 different "spaces" one was long that another when going through the file with the arrow keys. To confirm that if was binary, I expected the flag to be there. So in CyberChef i made an end curly bracket } and converted it using the "To Binary" operation. Now when looking at the last line and going through it, we notice that small spaces are zeros and the long ones are ones. As you can see below, i have replaced the long spaces with underscores and the small ones with a hyphen to make it easier to see.
- _ _ _ _ _ - _ <- transmission.txt content on last line
0 1 1 1 1 1 0 1 <- End curly bracket in binary (to match the ending of a flag)
To translate the whole file, i made a quick python script to print out all the lines as binary.
Python script:
with open("transmission.txt", "r") as f:
lines = f.readlines()
for line in lines:
bin_char = []
line = line.replace("\n", "")
for char in line:
if char == " ":
bin_char.append("0")
elif char == "\t":
bin_char.append("1")
print("".join(bin_char))
When copying the output of the file, you can paste it into CyberChef and use the "from binary" operation, and then you will se the flag.
Rick Sanchez Algorithm
Challenge Description
In and out morty a 20 second adventure
C = 9763756615749453697711832780290994218209540404092892743938023440562066399337084806157794233931635560977303517688862942257802526956879788034993931726625296410536964617856623732243706473693892876612392958249751369450647924807557768944650776039737608599803384984393221357912052309688764443108728369555676864557154290341642297847267177703428571478156111473165047499325994426058207523594208311563026561922495973859252628019530188566290941667031627386907620019898570109210940914849323148182914949910332546487694304519512036993844651268173759652768515378113523432311285558813699594606327838489283405761035709838557940909309
n = 25886873815836479531102333881328256781823746377127140122698729076485535125711666889354560018621629598913480717734088432525491694576333336789245603514248141818159233105461757115009985693551920113198731562587185893937220809465123357884500614412967739550998756643760039322502299417470414994227318221114452157902944737622386655242568227060393806757218477070728859359570853449231546318892600962043047963934362830601068072327572283570635649379318478675132647932890596210095121862798891396418206480147312633875596896359215713337014482857089996281525920299938916154923799963866283612072794046640286442045137533183412128422223
e = 3412227947038934182478852627564512970725877639428828744897413324202816073614248101081376540697482845313507125163089428254245096018283445899452858022211718628390653483026409446914537083191082941622293729786517851124468666633780447090080209520381218492938112166177839174421554838099214223129604698311531540363994640048732628930103674878115331383263452987483186144997440066159073515630319057855626746004248806849195662788941903776396118558065192757367266853647652706247900976106843337363721026272734784391404675859060134421742669727121306927682580867089725963848606261214171291213498225968719857795306299660931604391979Challenge Solution
This is a simple RSA encoded message, it can easily e decoded using RsaCtfTool or the even easier way, using www.dcode.fr/rsa-cipher an online decoder that is very easy to use. After filling out the information we have, you can press the "decrypt" button, and the flag will show up on the left hand side.
Web
Sanity Check In Space
Challenge Description
Man, web exploitation sure is fun. Sometimes you just need to go back to the basics, you know what I mean? Everything you need to get started on your journey to becoming a web master is here.
p.s: You can make anything space themed if you try hard enough.
http://scis.hackers.best:31337/
Challenge Solution
Go to the given web adress, the first page we see is welcome message and a picture of a robot. The picture is a hint. Many websites use robots.txt to keep google or other search engines from indexing some pages. When going to the url scis.hackers.best:31337/robots.txt we see the following piece of text:
Welcome to page two of Sanity Check in space, here's some robots.txt stuff. User-agent: * Disallow: humans.txt/
This says that humans.txt shouldn't be indexed, let's try to go to that page at scis.hackers.best:31337/humans.txt
Now we see a text that it has to be sure that we are a human. Also when looking at the big spaceman picture, we get a hint for what we can look at. The astronaut is holding a cookie, so let's take a look at them. In most, if not all browsers, you can view the cookies in the developer tools that is accessed by pressing F12, at least if you are using firefox.
We can see a field in the cookie that says human and it is set to false, let's try to edit it to say true and reload the page to see what happens.
Now the text on the page has changed, it now say "Wow, you really are human, celebrate with us by visiting arrakis", now let's try to go to chat page at scis.hackers.best:31337/arrakis
At the buttom of the page, there is a field for a password. Let's pull out the developer tools again, and look at the source. In the source we find a comment containing the password.
When you input the password, the text above the password box changes, and says that a challenge "awaits you on krypton". So now, let's go to krypton at scis.hackers.best:31337/krypton
Now we have a box that pings websites, so let's try to input a domain.
It looks like the input box takes a domain and uses the commandline to get the output seen on the website. Let's try to exploit this by adding some extra stuff after the domain. So now we can assume that the program runs the following ping <domain> in linux, you can run two commands in one input by adding && after the first command, so let's try to see if it works by inputting the following text google.com && ls
The theory is correct. It is indeed running the input in the terminal and we can see that there is a file called flag.txt in the current directory. We can quickly assume that this is the flag we need to get. Let's use the cat command this time to see the text inside the file. So our input will be google.com && cat flag.txt
Now at the buttom, we got the flag.
attack-strategies
Challenge Description
The StarCraft III Interplanetary Newbie Championship is almost live and I was assigned to take care of teaching everyone in the Newbie-84 planet how to play. I made a blog so each individual can choose their favorite races and strategies to learn before the tournament. I will secretly participate and to give them a change, I hid my go to strategy somewhere on the website. Wanna try finding it?
http://vespene-gas.hackers.best:31337/
Challenge Solution
After looking around the site and source, i notice that there is a cookie with a "show_hidden" key set to "false". By editting this value to "true" and reload the page, we now see a "flag.txt" folder in the dropdown menu.
It is important for this challenge to understand what folders a loaded into the dropdown. We can see a script in the html code of the website.
document.getElementById('folder_select').addEventListener('change', function() {
var folderSelect = document.getElementById('folder_select');
var fileSelect = document.getElementById('file_select');
var submitBtn = document.querySelector('input[type="submit"]');
var folder = folderSelect.value;
if (folder) {
fetch('/files/' + folder)
.then(response => response.json())
.then(data => {
fileSelect.innerHTML = '';
for (var i = 0; i < data.length; i++) {
var option = document.createElement('option');
option.value = data[i];
option.text = data[i];
fileSelect.appendChild(option);
}
fileSelect.disabled = false;
submitBtn.disabled = false;
});
} else {
fileSelect.innerHTML = '<option value="" selected>Select a file...</option>';
fileSelect.disabled = true;
submitBtn.disabled = true;
}
});This script shows that the folders are fetched from the /files/ directory, so let's try to access te flag that way.
Going to http://vespene-gas.hackers.best:31337/files/flag.txt returns an Internal server error, while http://vespene-gas.hackers.best:31337/files/General doesn't. When going back to the main page of the site and selecting a folder and a file and pressing the View button, we see that the page makes a request POST request with some form data. For the General folder and "Cannon Rush" file, the Post request form data looks like this:
folder_select=General&file_select=Cannon+RushBy changing the folder_select and file_select in the post request, we might be able to extract the flag.txt from the /files folder.
I don't know a tool in firefox that will make this process easier, so i will use the Burpsuite proxy for this.
So before enabling the intercept feature, i first select the folder and some file. Then enable the intercept feature, and press the view button.
Then your request should look something like this.
In the red cirkel you will need to edit the data, so that we can get the flag. The folder_select value should be . (a dot), to indicate that we want a file from the current directory, and the the file should be flag.txt like in the image below.
Then forward the request, and you should be able to see the flag in the browser.
Forensics
A New Hope
Challenge Description
Princess Leia has been kidnapped! She managed to send a message to this droid we have recovered. It was damaged while we were recovering it however. It seems that sometimes you have to tear something down, in order to build them back up.
Can you recover the message?
Challenge Solution
Opening up the powerpoint reveals nothing special. We see some images, nothing really useful. So let's dig deeper. Some know, that powerpoint files are just a .zip folder containing the data represented in the powerpoint program. We can rename the folder to see what files it has.
After some digging around, you may have seen an image in the /ppt/media folder called image1.png that can't be opened, this might be where the flag is hidden. Since the image is corrupted, we need to fix it, so let's try to use the hexedit command so we can fix the file. To open the file in hexedit, you simple use the following command hexedit image1.png.
This reveals something interesting. We notice that the file starts with 4 zeros, which it shouldn't do. Also, the file name image1.png doesn't match the "JFIF" file signature found in the hex data of the image file. Now let's fix the file. I usually use this website to find file signatures. Let's seach for JFIF on the site to find the starting hex values of a JFIF (jpeg) file.
Now that we know how the file should start, we can fix it. Open hexedit again and fix the first 4 hex values. Save it by pressing CTRL+S.
Now you should be able to open the image, if not, try to change the file extension from .png to .jpeg.
And there you have the flag, at the top of the image.
Time Leap
Challenge Description
You've just been hired as one of SERN's "Rounders". We've been studying time travel technology, but we're having an issue generating Kerr Black Holes. We can't figure out how to configure our ionic lifter properly. We've discovered that a certain man in Tokyo managed to figure it out. After raiding his lab, you found a USB drive that probably has some useful information on it.
Challenge Solution
Download the challenge file, and extract it using the gunzip command. When extracted, you will need to mount the disk image. You can do this by creating a new folder where you want the files to appear, and then using the following command sudo mount convergence.img <some_folder>
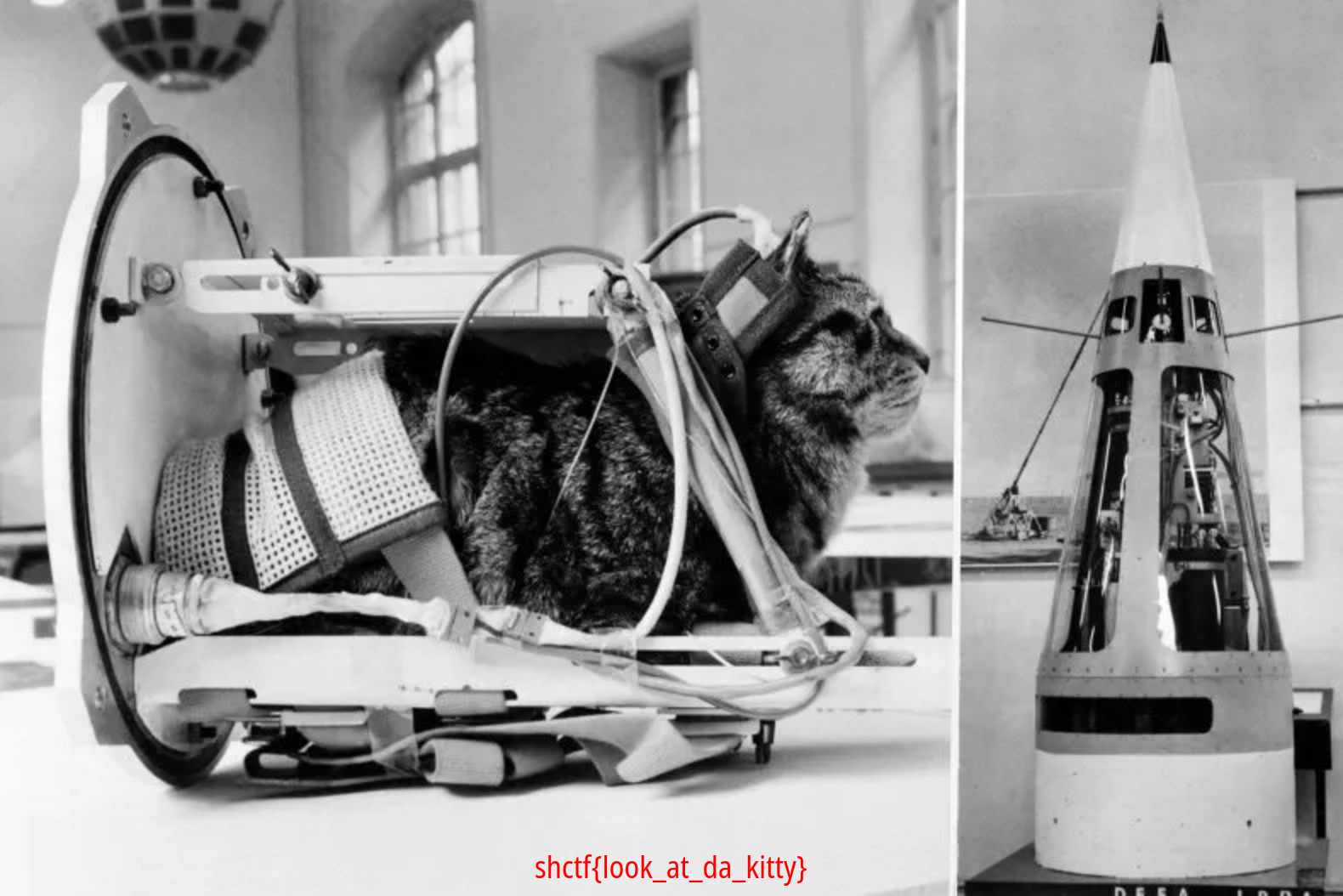
Félicette
Challenge Description
a cat in space, eating a croissant, while starting a revolution.
Challenge Solution
In the wireshark capture file i noticed that the large amount of data was a file stream, it was sending an image, i noticed this by looking at some of the first packets sent, that matched the jpeg file signature. When i knew this, i could start making the python script that could take the many packets and piece them together to form an image. Scapy is needed here to load the wireshark file.
from scapy.all import rdpcap
packets = rdpcap("chall.jpg.pcap")
hex_data = []
for packet in packets:
hex_data.append(packet.lastlayer().fields['load'])
with open("Felicette.jpg", "wb") as f:
for i in hex_data:
f.write(i)Now when running this script, we get the output jpg file with a flag in it.
space_stream
Challenge Description
Our recon troops gathered information about the enemy territory and reported back to our Planetary Fortress. However, Zerg's Red team hackers infiltraded our database and hid all information about where their main Lair is located. Can you recover the missing image for us?
Challenge Solution
Whenever i have been given a virtual disk file, i either mount it, if we know that the data is intact, or use a tool like Autopsy or testdisk a linux CLI tool that can also recover files. The description hints that there is a missing file, so for this i will use testdisk, but you can also use autopsy if you are on windows.
So to use testdisk on the file, we simple run the first command testdisk startstream.vhd. Testdisk will ask for what disk to use, and since there is only one, we just proceed by pressing Enter.
Testdisk will automatically detect the filesystem and preselect the partition table type we want to use.
Press Enter to select the detected partion type, and then press enter again to analyse the disk, and then again to perform a quick search. When it has performed the scan, press Shift + P to list the files in the virtual disk. Press a to select all files.
Then press Shift + C to copy (extract) the selected files.
Now you need to select where to place the files that you have selected, i will just go with the default option to store it i nthe same directory as the virtual disk file. When you have selected the save location, press Shift + C.
You should now see the confirmation, that te files were saved successfully and be able to see them in the save location.
We are done with testdisk now, it can just be closed. Let's look at the files we extracted. You can ignore the data_streams:stream5.zip file, this is just a copy of the zip file found in the data_streams folder.
I noticed that when i extracted the zip file stream5.zip located in the data_streams folder, a pdf appears, but can't be opened because it's password protected.
Let's keep this in mind when going through the data_streams folder. I am not sure if testdisk does this for us, but it looks like it extracted text files from the different pictures because the text files are named stream1.jpg:sarah_kerrigan, but this makes the process a lot quicker for us, because opening the file stream1.jpg:sarah_kerrigan hints that the user uses her name as her password. So we assume that sarah_kerrigan, could be the password.
Minor note: When the CTF ended, some people said that half of the pdf was missing, and this could be because of the tool they used to open the pdf. My kali installation defaults pdf's to open in firefox and i can see the whole pdf file.
When copying in the password, we see that it was correct, we opened the pdf file and can see the flag at the left side.
My God, it's full of .- ... -.-. .. ..
Challenge Description
If sound can't travel in a vacuum then how did a microphone pick this up in space unless space is a made up concept designed to make us fear leaving Earth and joining with Xenu and the Galactic Confederacy?
Challenge Solution
I really hope there is a tool for this, i couldn't fin one, so this solution is kinda scuffed... So we have been given an audio file, and the challenge title suggests that it's morse code, but it's not. Upon closer inspection in Sonic Visualizer, it seems like it could be binary bumps in the audio track. Aaand indeed it is...
In the audio track (with some fine adjusting in zoom) you can see something like in the picture below.
You can see that there are large spaces that seperates each binary block, and thin/thicc blocks representing a 0 or 1. Because I don't know if there is a tool for this, i did it by hand... When reading it all, you get all this binary code:
01110011 01101000 01100011 01110100 01100110 01111011 01001110 00110000 00100000 00110001 00100000 01100011 00110100 01101110 00100000 01001000 00110011 00110100 01110010 00100000 01110101 00100000 00111000 00110011 00110011 01010000 01011111 00111000 00110000 00110000 01110000 00101000 01001001 01101110 00101001 00100000 00111100 00100000 00101111 01100100 01100101 01110110 00101111 01101110 01110101 01101100 01101100 01110011 01110000 01100001 01100011 01100101 01111101Now to convert it to a flag, we just put it into CyberChef and use the "From binary" operation, and then you have the flag.
Please let me know if there is a tool for this.
